Simple instructions on how to fix the “Bash Software Bug" (Shellshock Bash Vulnerability) and the biggest threat since “Heartbleed”, using open-source command-line package-management utility YUM (yellowdog updater). Below instructions will work on CentOS & Red Hat. Other Linux systems such as Scientific Linux, Yellow Dog Linux, Oracle Linux and those using the RPM Package Manager currently do not have the patch available (at the time of this article - 24.Sept.2014) but that should be coming soon. In any case instructions posted below will work for these other Linux distros as soon as the patch is available.
Note: Shellshock Bash Vulnerability was described in CVE-2014-6271 / RHSA-2014:1293-1.
So how do we fix the issue? Fix is fairly simple, you need to update 'bash' (The GNU Bourne Again shell) from whatever version you're currently running to version 4.1.2-15.el6_5.1 or higher.
- First run following command to see what version of Bash you're currently running:
bash --version
or if you want to separate the version number by highlighting it in a different color, use this command:
rpm -qa | grep --color bash
Additionally, for the sake of having multiple options, you can also retrieve Bash version using any of these commands:
rpm -q bash
yum info bash
yum list installed bash
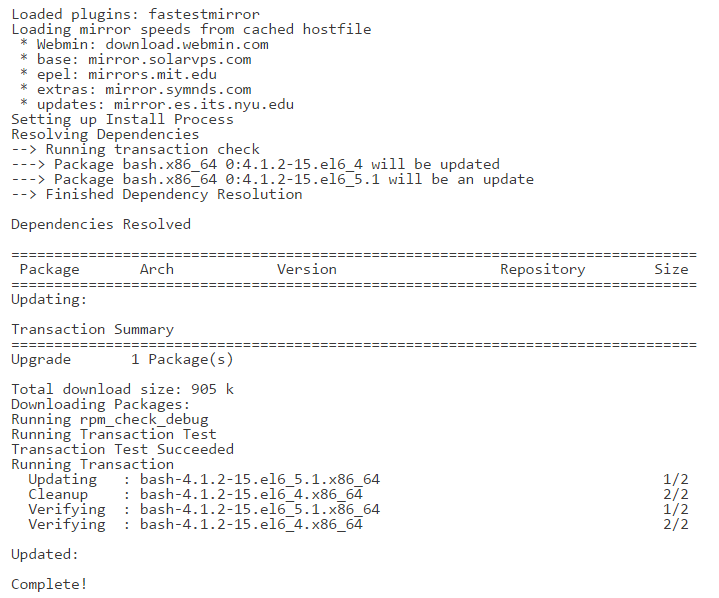
- If the output shows version older than 4.1.2-15.el6_5.1, you'd need upgrade bash to its most recent version. If that's the case, then execute the following YUM command:
yum update bash
This is what a successful result should look like:
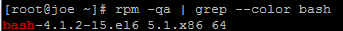
Once done, run following command again, to confirm that you're using the most recent version of bash:
rpm -qa | grep --color bash
Output should look like this, confirming you're using 4.1.2-15.el6_5.1 or higher:
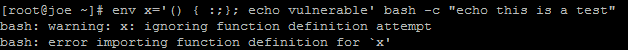
To make sure that the patch has worked, test it using following command:
env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
A patched shell will return:
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for `x'
This is what it'll look like in your shell:
You can also test your domain for Shellshock Bash vulnerability using following website: http://shellshock.iecra.org/
I hope this helps. If you want to leave me a message, use the comment box below.
--
Here is a short video briefly explaining Shellshock bug: